Navigating the SOCI Act – 3 tips to achieve cyber security compliance
Australian industry is undergoing a digital revolution. Information Technology (IT) and Operational Technology (OT) environments are increasingly becoming interconnected across a multitude of industries dealing with critical infrastructure, enabling significant business efficiencies but also opening up risks to cyber-attacks.
Cyber security is already a must-have for every organisation to ensure important assets and data are safeguarded, but there is an added degree of urgency for companies dealing with critical assets and infrastructure. To ensure customers of Australian Critical Infrastructure Suppliers are better protected against the risk of a cyber breach, the Australian Federal Government introduced the Security of Critical Infrastructure (SOCI) Act in 2018 to improve the cyber security protection and resilience of the Critical National Infrastructure (CNI) industry sector.
Do you have obligations under the SOCI Act?
If you’re in an Australian industry that deals with critical infrastructure – most likely!
Initially focussed on the physical security of traditional critical infrastructure assets, the SOCI Act was amended in 2021 and 2022 to more appropriately capture those assets that are critical to Australia’s defence, national security, and economic and social stability. In addition, it increased the number of Critical Infrastructure Sectors (CIS) with cyber security obligations from 3 to 11 and introduced new mandatory reporting requirements.
The 11 sectors with direct SOCI Act obligations (at the time of publishing) are:
- Communications,
- Data storage or processing,
- Financial services and markets,
- Water and sewerage,
- Energy,
- Health care and medical,
- Higher education and research,
- Food and grocery,
- Transport,
- Space technology, and,
- Defence industry.
The SOCI Act now requires organisations that own, operate or supply services to these 11 sectors identified in the Act to implement cyber security measures and report any security incidents to the government. The new Positive Security Obligations (PSO) amended in the Act include:
- Maintaining a register of critical assets,
- Mandatory cyber incident reporting, and,
- Adopt, maintain and comply with a critical infrastructure Risk Management Program.
For many organisations dealing with Australian critical infrastructure, the SOCI Act is a compliance requirement and therefore is compulsory. Despite being a necessary and critical measure in cyber security, understanding all the requirements can be challenging and some organisations find themselves making assumptions about how it impacts them rather than knowing how to achieve compliance.
Three simple tips to achieve SOCI Act compliance
There are several steps required to achieve an effective cyber and information security system that adheres to the requirements of the SOCI Act, and, in this blog, we’ll introduce three simple tips that organisations can leverage to effectively comply with the SOCI Act to help build your path towards compliance and enhancing cyber security in the process.
NOTE: This blog is designed to support your initial research and planning to better understand your obligations. If you are unsure whether your asset may be subject to the various SOCI Act obligations, please visit the Regulatory Obligations page on the Cyber and Infrastructure Security Centre website, which includes updated guidance material to assist.
Tip 1: Identify and understand your critical assets.

The first step towards achieving SOCI Act compliance is to identify the critical assets within your organisation. This includes the physical and digital systems that are essential for the functioning of your organisation and its services, including both IT and OT assets.
The Cyber and Infrastructure Security Centre (CISC) maintains a register of information about critical infrastructure assets. This information supports the Government in identifying and managing risks that could potentially cause significant harm to Australia.
Some examples of IT and OT assets include:
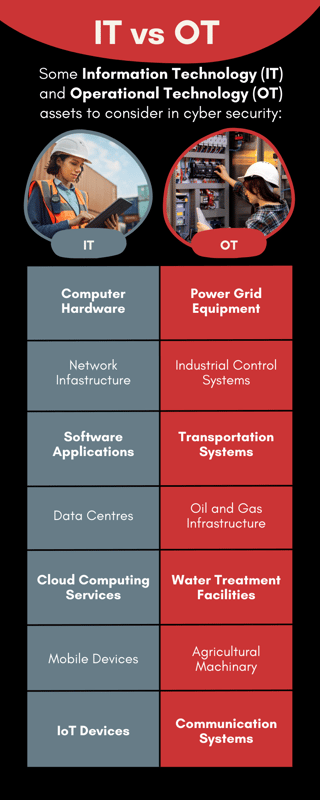
For more information about your obligations please visit the Register of Critical Infrastructure Assets Guidance page on the Cyber and Infrastructure Security Centre website.
Tip 2: Monitor and report cyber security incidents.

The SOCI Act provides for mandatory cyber incident reporting for critical infrastructure assets. A cyber security incident is defined as one or more acts, events or circumstances involving:
- Unauthorised access to or modification of computer data or computer programs,
- Unauthorised impairment of electronic communications to or from a computer, or,
- Unauthorised impairment of the availability, reliability, security or operation of computer data, a computer program or a computer.
The ACT describes a critical cyber security incident that has occurred, or is occurring, and whether the incident has had or is having a significant impact on the availability of your asset. If a cyber security incident is identified as being critical, you must notify the ACSC within 12 hours of becoming aware of the incident. For example, a critical cyber security incident might impact an electricity asset’s operational technology, which impacts the generation, transmission, or distribution of electricity.
The ACT also describes other cyber security incidents that have occurred or are occurring, and the '"relevant impact" they have had or are having on your assets. Upon identifying that an incident is causing a relevant but not critical impact, you must notify the ACSC within 72 hours of becoming aware of the incident. For example, a cyber security incident might impact a bank’s information technology (e.g., corporate network) in a manner that could expose information about the asset, but not compromise the provision of banking services.
For more information about your Cyber Security Incident Reporting obligations please visit the Cyber Security Incident Reporting page on the Cyber and Infrastructure Security Centre website.
Tip 3: Implement a cyber security framework.

There are multiple cyber security frameworks available to help guide organisations with their SOCI Act compliance efforts, providing a comprehensive set of recommendations and best practices for organisations to implement and improve their cyber security posture.
Under the new Positive Security Obligations (PSO) released in February 2023, critical asset owners must establish and maintain a process or system to comply with one of the below specified cyber and information security frameworks/standards or an equivalent framework:
- AS/ISO 27001:2015 (Australian Standard that directly adopts the requirements of ISO 27001),
- NIST - CSF (National Institute of Science and Technology - Cyber Security Framework),
- AESCSF (Australian Energy Sector Cyber Security Framework. Requirement to meet Security Profile 1),
- Essential Eight Maturity Model (published by the ASD. Requirement to meet Maturity Level one), or,
- C2M2 (Cyber Capability Maturity Model. Requirement to meet Maturity Indicator Level 1).
The purpose of this requirement is to ensure asset owners meet a minimum baseline level of cyber and information security for their critical infrastructure assets. Importantly, compliance with the above cyber security framework (or equivalent) is required to be established by the 17th of August 2024.
Where to next?
If you have obligations under the SOCI Act, it’s crucial to comply, for the safety of your organisation and to ensure the ongoing safety of Australia’s critical infrastructure. In February 2023, the Security of Critical Infrastructure Rules (LIN 23/006) 2023 outlined that the 11 CIS will be required to implement a Critical Infrastructure Risk Management Program (CIRMP).
Following an initial 6-month period for transition beginning on the date of commencement (17 February 2023), the first reports will be required within 90 days following 30 June 2024. Read the Risk Management Program Rules of Critical Infrastructure Assets Guidance provided by the Cyber and Infrastructure Security Centre to learn more about the new requirements.
The three tips outlined in this blog are a great start toward looking internally at your current cyber security positioning, but if you want to take it a step further, SAGE Cyber Security can help. The SAGE SOCI Act Review Service is the first step to reaching a higher level of cyber security to meet the compliance requirements of the SOCI Act and delivers a structured roadmap for the initial phases of that journey.
The service includes:
- A current state assessment against the requirements of the SOCI Act and the recent reforms by reviewing existing controls and artifacts and conducting interviews with key stakeholders.
- A risk assessment based on the outcomes to determine a prioritised list of activities and roadmap to achieve compliance.
Reach out if you would like to learn more, or for further cyber security reading, check out the 5 basics to ensure cyber resilience in Operational Technology (OT).







.webp?width=457&height=173&name=Sage-Group-Embedded-Expertise-Logo(1).webp)